Envoy GCP Authentication Filter with Application Layer Transport Security (ALTS)
2022-05-23This is a sample configuration of Envoy’s GCP Authn Filter combined with Application Layer Transport Security.
What the GCP Auth Filter does is simple: it accesses the current GCP VM’s identity token and automatically injects that into the Authorization Bearer header intended for the upstream server. It basically allows the server to verify the client by using its bearer token that is unique to that instance.
Theres nothing stopping you from manually getting an id_token manually by the client but this way, it can be automatically sanitized (redacted by envoy) and ammended by any audience value the server-to-server communication needs.
Since this envoy proxy filter is GCP specific, the client VM must be on GCE (or any other system that has a metadata server on GCP).
However, the server does not need to be on gcp…it can be any system capable of verifying an inbound id_token. It can be on GCP, on prem, anywhere.
Great…but we’re talking about bearer tokens…one problem with that is implied within its name: bearer..meaning its authenticates anyone with that presents it. What happens if the token is used by different system than the one that issued it? Well, at that point, the other system can pretend to be the tokens creator.
Is there anyway we can compensate for a bearer tokens deficiency?
Sure, but its not easy: you can attempt to configure Certificate Bound Tokens but getting that setup is pretty hard. You can go one step easier by using a distribution of mTLS certificates like what google does with Traffic Director
To me, thats fine but i want to combine this new Feature of envoy with ALTS …which i find really, really cool..
Taken together, the ALTS layer verifies to the server and client the service identity and the JWT bearer token signals the what the token can be used for (eg the service’s aud: value, its expiration, claims, instance id)
note, ther’es only one implementation of ALTS in the world that i know of: its on Google….so take this demo with a grain of salt..
Realistically, you’ll want to use one of those services like Traffic Director or just use the GCP Authn plugin as a basic bearer token.
If you’re still interested in ALTS, see Envoy ALTS Helloworld
For now, we’ll just setup two GCE VMs:
-
Client Runs envoy with GCP Authn Filter Uses ALTS to connect to Server
-
Server Runs envoy with JWTAuthn Filter Uses ALTS to only allow connections from Client
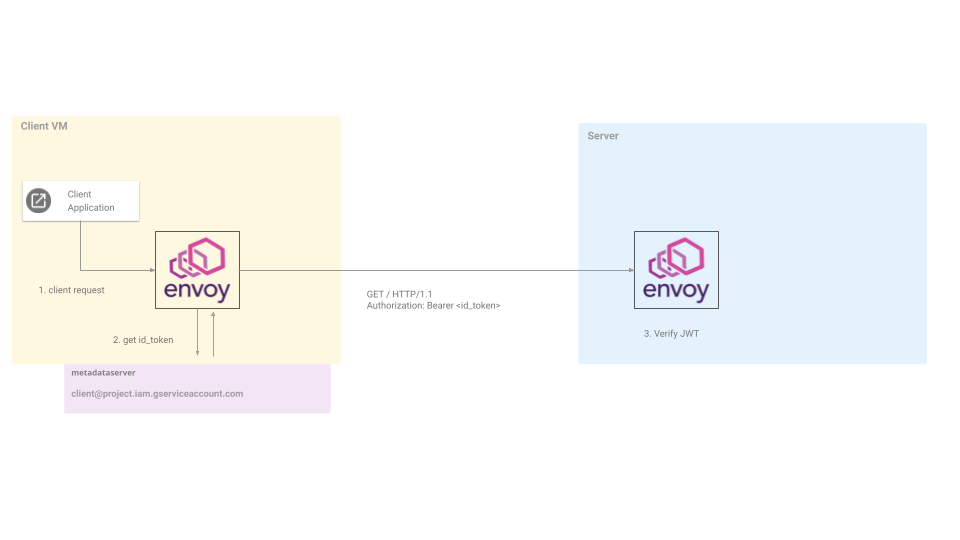
Envoy GCP Authn Filter
Lets get started
First lets look at the Client configuration for Envoy minus the ALTS business:
Note that the http_filter.envoy.filters.http.gcp_authn sets up where to get an id_token.
The URL provided there is for the GCE VM’s metadata server. The [AUDIENCE] key is special: the filter uses that exact text and substitutes the value for the audience this id_token should have. Typically, this needs to be the service this token is intended (in our case, its the server).
The value for the audience is read by the Filter by inspecting the cluster the filter is meant to contact. In our case its read in from the Audience.url value in
service_b.
node:
cluster: service_greeter
id: test-id
static_resources:
listeners:
- name: listener_0
address:
socket_address: { address: 0.0.0.0, port_value: 8080 }
filter_chains:
- filters:
- name: envoy.http_connection_manager
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.network.http_connection_manager.v3.HttpConnectionManager
stat_prefix: ingress_http
codec_type: AUTO
route_config:
name: local_route
virtual_hosts:
- name: backend
domains:
- "server.c.$PROJECT_ID.internal"
routes:
- match:
prefix: "/get"
route:
cluster: service_b
http_filters:
- name: envoy.filters.http.gcp_authn
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.http.gcp_authn.v3.GcpAuthnFilterConfig
http_uri:
uri: "http://metadata.google.internal/computeMetadata/v1/instance/service-accounts/default/identity?audience=[AUDIENCE]"
cluster: metadata_server
timeout: 1s
- name: envoy.filters.http.router
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.http.router.v3.Router
clusters:
- name: metadata_server
type: STRICT_DNS
dns_lookup_family: V4_ONLY
connect_timeout: 2s
lb_policy: ROUND_ROBIN
load_assignment:
cluster_name: metadata_server
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address:
address: metadata.google.internal
port_value: 80
- name: service_b
type: LOGICAL_DNS
dns_lookup_family: V4_ONLY
connect_timeout: 2s
lb_policy: ROUND_ROBIN
metadata:
typed_filter_metadata:
envoy.filters.http.gcp_authn:
"@type": type.googleapis.com/envoy.extensions.filters.http.gcp_authn.v3.Audience
url: "server.c.$PROJECT_ID.internal"
load_assignment:
cluster_name: service_b
endpoints:
- lb_endpoints:
- endpoint:
address:
socket_address:
address: server.c.$PROJECT_ID.internal
port_value: 10000
Ultimately, this id token that is sent to service_b will look like
{
"alg": "RS256",
"kid": "486f16482005a2cdaf26d9214018d029ca46fb56",
"typ": "JWT"
}
{
"aud": "server.c.YOUR_PROJECT.internal",
"azp": "105358594526781723383",
"exp": 1653426840,
"iat": 1653423240,
"iss": "https://accounts.google.com",
"sub": "105358594526781723383"
}
where the aud value is what was set in clusters.service_b.metadata.typed_filter_metadata.envoy.filters.http.gcp_authn.url
(The way envoy shares metadata between filters is kinda complicated to me, see data shared between filters)
One more thing about the JWT…google’s id_token can contain many other claims
Specifically, the extended claims can signal to the server what the nature (licenses, Confidential Compute state instance_confidentiality, and so on). The server can use these values to make further decisions.
{
"iss": "[TOKEN_ISSUER]",
"iat": [ISSUED_TIME],
"exp": [EXPIRED_TIME],
"aud": "[AUDIENCE]",
"sub": "[SUBJECT]",
"azp": "[AUTHORIZED_PARTY]",
"google": {
"compute_engine": {
"project_id": "[PROJECT_ID]",
"project_number": [PROJECT_NUMBER],
"zone": "[ZONE]",
"instance_id": "[INSTANCE_ID]",
"instance_name": "[INSTANCE_NAME]",
"instance_creation_timestamp": [CREATION_TIMESTAMP],
"instance_confidentiality": [INSTANCE_CONFIDENTIALITY],
"license_id": [
"[LICENSE_1]",
...
"[LICENSE_N]"
]
}
}
}
If you want the outbound JWT to contain these, change the value in envoy to
uri: "http://metadata.google.internal/computeMetadata/v1/instance/service-accounts/default/identity?audience=[AUDIENCE]&format=full"
Setup
Lets get setup…to do this demo you’ll need two GCE VMs…i have to emphasize again, the server can be anywhere but if the server is NOT in GCE, you must remove the ALTS configuration….since, of course, ALTS exists only on GCP :)
export PROJECT_ID=`gcloud config get-value core/project`
export PROJECT_NUMBER=`gcloud projects describe $PROJECT_ID --format='value(projectNumber)'`
# create two service accounts
gcloud iam service-accounts create server-sa --display-name "Server Service Account"
gcloud iam service-accounts create client-sa --display-name "Client Service Account"
export CLIENT_SERVICE_ACCOUNT=client-sa@$PROJECT_ID.iam.gserviceaccount.com
export SERVER_SERVICE_ACCOUNT=server-sa@$PROJECT_ID.iam.gserviceaccount.com
# create two VM's and attach service accounts to each
gcloud compute instances create server \
--service-account=$SERVER_SERVICE_ACCOUNT \
--scopes=https://www.googleapis.com/auth/userinfo.email \
--zone us-central1-a --image-family debian-10 --image-project=debian-cloud
gcloud compute instances create client \
--service-account=$CLIENT_SERVICE_ACCOUNT \
--scopes=https://www.googleapis.com/auth/userinfo.email \
--zone us-central1-a --image-family debian-10 --image-project=debian-cloud
Now create the envoy configuration files with the PROJECT_ID values you need.
You can find the files below in this article. Be careful in naming each file thats you download
envsubst < "server_tmpl.yaml" > "server.yaml"
envsubst < "client_tmpl.yaml" > "client.yaml"
Get envoy binary.
I usually get it through docker
docker cp `docker create envoyproxy/envoy-dev:latest`:/usr/local/bin/envoy .
Copy the files to the client and server
gcloud compute scp envoy server:
gcloud compute scp envoy server:
gcloud compute scp server.yaml server:
gcloud compute scp client.yaml client:
Start Server
gcloud compute ssh server
./envoy -c server.yaml -l trace
Start Client
gcloud compute ssh client
./envoy -c client.yaml -l trace
Run Curl Client
In a new terminal on the client:
gcloud compute ssh client
export PROJECT_ID=`gcloud config get-value core/project`
curl -v -H "Host: server.c.$PROJECT_ID.internal" http://localhost:8080/get
What you should see is a simple, measly ok…but a lot went on under the hood as shown in the logs
Configuration
Client
client_tmpl.yaml
Server
server_tmpl.yaml
Logs
As for logs, i’ve annotated each step as the best i can and redacted the noise
Client
============================== Client Request
[2022-05-24 20:14:00.801][645][debug][conn_handler] [source/server/active_tcp_listener.cc:142] [C0] new connection from 127.0.0.1:33474
[2022-05-24 20:14:00.801][645][debug][http] [source/common/http/conn_manager_impl.cc:904] [C0][S13822938871470853975] request headers complete (end_stream=true):
':authority', 'server.c.YOUR_PROJECT.internal'
':path', '/get'
':method', 'GET'
'user-agent', 'curl/7.64.0'
'accept', '*/*'
============================== Metadata Server Request
[2022-05-24 20:14:00.802][645][debug][router] [source/common/router/router.cc:467] [C0][S11072735566668962897] cluster 'metadata_server' match for URL '/computeMetadata/v1/instance/service-accounts/default/identity?audience=server.c.YOUR_PROJECT.internal'
[2022-05-24 20:14:00.802][645][debug][router] [source/common/router/router.cc:670] [C0][S11072735566668962897] router decoding headers:
':method', 'GET'
':authority', 'metadata.google.internal'
':path', '/computeMetadata/v1/instance/service-accounts/default/identity?audience=server.c.YOUR_PROJECT.internal'
':scheme', 'http'
'metadata-flavor', 'Google'
'x-envoy-internal', 'true'
'x-envoy-expected-rq-timeout-ms', '1000'
[2022-05-24 20:14:00.802][645][debug][pool] [source/common/conn_pool/conn_pool_base.cc:290] trying to create new connection
[2022-05-24 20:14:00.802][645][debug][connection] [source/common/network/connection_impl.cc:912] [C1] connecting to 169.254.169.254:80
[2022-05-24 20:14:00.813][645][trace][http] [source/common/http/http1/codec_impl.cc:1353] [C1] status_code 200
[2022-05-24 20:14:00.813][645][debug][http] [source/common/http/async_client_impl.cc:101] async http request response headers (end_stream=false):
':status', '200'
'metadata-flavor', 'Google'
'date', 'Tue, 24 May 2022 20:14:00 GMT'
'content-type', 'text/html'
'server', 'Metadata Server for VM'
'content-length', '682'
'x-xss-protection', '0'
'x-frame-options', 'SAMEORIGIN'
'x-envoy-upstream-service-time', '11'
[2022-05-24 20:14:00.813][645][debug][router] [source/common/router/router.cc:467] [C0][S13822938871470853975] cluster 'service_b' match for URL '/get'
[2022-05-24 20:14:00.813][645][debug][router] [source/common/router/router.cc:670] [C0][S13822938871470853975] router decoding headers:
':authority', 'server.c.YOUR_PROJECT.internal'
':path', '/get'
':method', 'GET'
':scheme', 'http'
'user-agent', 'curl/7.64.0'
'accept', '*/*'
'x-forwarded-proto', 'http'
'x-request-id', '434e144c-0732-4227-8f6a-781f609d08df'
'authorization', 'Bearer eyJhbGciOiJSUzI1NiIsImtpZCI6IjQ4NmYxNjQ4MjAwNWEyY2RhZjI2ZDkyMTQwMThkMDI5Y2E0NmZiNTYiLCJ0eXAiOiJKV1QifQ.eyJhdWQiOiJzZXJ2ZXIuYy5taW5lcmFsLW1pbnV0aWEtODIwLmludGVybmFsIiwiYXpwIjoiMTA1MzU4NTk0NTI2NzgxNzIzMzgzIiwiZXhwIjoxNjUzNDI2ODQwLCJpYXQiOjE2NTM0MjMyNDAsImlzcyI6Imh0dHBzOi8vYWNjb3VudHMuZ29vZ2xlLmNvbSIsInN1YiI6IjEwNTM1ODU5NDUyNjc4MTcyMzM4MyJ9.c-zxdjjUPT7B7g9BlHFjYj2bVnCksr0RNuGtF2I-ln3dcAzgu1pd_E-zoWR-KwJDZOuSMPDcjUea75DUt5ps4TwbHFyZ1x5GD3BRArl1Ts0p_QAtND-elV2c_ZDk-txpGCkI2ESGKszjv5_UF_aiIeO5l344ECB_zERD5LA3BeXoVDix-v5uw0KLFjZM03OBcNbItdy1B7dNIGUqOZNpRp2PWXxY5ppf33BXXY3U_JepzK0qynZCvlPAeSJKqIc5LKpPBauzUYOYq0VH1xkL_SdfDgvoSCi69Eqgu9i3qNSaV8B7mdYO5mrfxsaE9SroKR2P0PdyEt-n2HkrqQAZ7w'
'x-envoy-expected-rq-timeout-ms', '15000'
============================== ALTS
[2022-05-24 20:14:00.822][645][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:103] [C2] TSI: Handshake successful: peer properties: 5
[2022-05-24 20:14:00.822][645][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:106] [C2] certificate_type: ALTS
[2022-05-24 20:14:00.822][645][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:106] [C2] service_account: server-sa@YOUR_PROJECT.iam.gserviceaccount.com
[2022-05-24 20:14:00.822][645][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:106] [C2] alts_context:
grpcALTSRP_GCM_AES128_REKEY"5server-sa@YOUR_PROJECT.iam.gserviceaccount.com*5client-sa@YOUR_PROJECT.iam.gserviceaccount.com2
[2022-05-24 20:14:00.822][645][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:106] [C2] security_level: TSI_PRIVACY_AND_INTEGRITY
[2022-05-24 20:14:00.822][645][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:113] [C2] TSI: Handshake validation succeeded.
[2022-05-24 20:14:00.822][645][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:125] [C2] TSI hanshake with peer: server-sa@YOUR_PROJECT.iam.gserviceaccount.com
[2022-05-24 20:14:00.822][645][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:144] [C2] TSI: Handshake successful: unused_bytes: 0
============================== Server Response
[2022-05-24 20:14:00.839][645][trace][http] [source/common/http/http1/codec_impl.cc:1353] [C2] status_code 200
[2022-05-24 20:14:00.839][645][debug][http] [source/common/http/conn_manager_impl.cc:1516] [C0][S13822938871470853975] encoding headers via codec (end_stream=false):
':status', '200'
'content-length', '2'
'content-type', 'text/plain'
'date', 'Tue, 24 May 2022 20:14:00 GMT'
'server', 'envoy'
'x-envoy-upstream-service-time', '25'
[2022-05-24 20:14:00.840][645][debug][client] [source/common/http/codec_client.cc:126] [C2] response complete
Server Logs
============================== Client Request
[2022-05-24 20:14:00.815][629][debug][conn_handler] [source/server/active_tcp_listener.cc:142] [C0] new connection from 10.128.0.17:36394
============================== ALTS
[2022-05-24 20:14:00.818][629][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:47] [C0] TSI: doHandshake
[2022-05-24 20:14:00.828][629][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:103] [C0] TSI: Handshake successful: peer properties: 5
[2022-05-24 20:14:00.828][629][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:106] [C0] certificate_type: ALTS
[2022-05-24 20:14:00.828][629][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:106] [C0] service_account: client-sa@YOUR_PROJECT.iam.gserviceaccount.com
[2022-05-24 20:14:00.828][629][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:106] [C0] alts_context:
grpcALTSRP_GCM_AES128_REKEY"5client-sa@YOUR_PROJECT.iam.gserviceaccount.com*5server-sa@YOUR_PROJECT.iam.gserviceaccount.com2
[2022-05-24 20:14:00.828][629][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:106] [C0] security_level: TSI_PRIVACY_AND_INTEGRITY
[2022-05-24 20:14:00.828][629][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:113] [C0] TSI: Handshake validation succeeded.
[2022-05-24 20:14:00.828][629][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:125] [C0] TSI hanshake with peer: client-sa@YOUR_PROJECT.iam.gserviceaccount.com
[2022-05-24 20:14:00.828][629][debug][connection] [source/extensions/transport_sockets/alts/tsi_socket.cc:144] [C0] TSI: Handshake successful: unused_bytes: 0
============================== Client Request
[2022-05-24 20:14:00.828][629][debug][http] [source/common/http/conn_manager_impl.cc:904] [C0][S2732626836338267029] request headers complete (end_stream=true):
':authority', 'server.c.YOUR_PROJECT.internal'
':path', '/get'
':method', 'GET'
'user-agent', 'curl/7.64.0'
'accept', '*/*'
'x-forwarded-proto', 'http'
'x-request-id', '434e144c-0732-4227-8f6a-781f609d08df'
'authorization', 'Bearer eyJhbGciOiJSUzI1NiIsImtpZCI6IjQ4NmYxNjQ4MjAwNWEyY2RhZjI2ZDkyMTQwMThkMDI5Y2E0NmZiNTYiLCJ0eXAiOiJKV1QifQ.eyJhdWQiOiJzZXJ2ZXIuYy5taW5lcmFsLW1pbnV0aWEtODIwLmludGVybmFsIiwiYXpwIjoiMTA1MzU4NTk0NTI2NzgxNzIzMzgzIiwiZXhwIjoxNjUzNDI2ODQwLCJpYXQiOjE2NTM0MjMyNDAsImlzcyI6Imh0dHBzOi8vYWNjb3VudHMuZ29vZ2xlLmNvbSIsInN1YiI6IjEwNTM1ODU5NDUyNjc4MTcyMzM4MyJ9.c-zxdjjUPT7B7g9BlHFjYj2bVnCksr0RNuGtF2I-ln3dcAzgu1pd_E-zoWR-KwJDZOuSMPDcjUea75DUt5ps4TwbHFyZ1x5GD3BRArl1Ts0p_QAtND-elV2c_ZDk-txpGCkI2ESGKszjv5_UF_aiIeO5l344ECB_zERD5LA3BeXoVDix-v5uw0KLFjZM03OBcNbItdy1B7dNIGUqOZNpRp2PWXxY5ppf33BXXY3U_JepzK0qynZCvlPAeSJKqIc5LKpPBauzUYOYq0VH1xkL_SdfDgvoSCi69Eqgu9i3qNSaV8B7mdYO5mrfxsaE9SroKR2P0PdyEt-n2HkrqQAZ7w'
'x-envoy-expected-rq-timeout-ms', '15000'
============================== JWT Verify
[2022-05-24 20:14:00.828][629][debug][jwt] [source/extensions/filters/http/jwt_authn/authenticator.cc:144] google-jwt: startVerify: tokens size 1
[2022-05-24 20:14:00.828][629][debug][jwt] [source/extensions/filters/http/jwt_authn/authenticator.cc:157] google-jwt: Parse Jwt eyJhbGciOiJSUzI1NiIsImtpZCI6IjQ4NmYxNjQ4MjAwNWEyY2RhZjI2ZDkyMTQwMThkMDI5Y2E0NmZiNTYiLCJ0eXAiOiJKV1QifQ.eyJhdWQiOiJzZXJ2ZXIuYy5taW5lcmFsLW1pbnV0aWEtODIwLmludGVybmFsIiwiYXpwIjoiMTA1MzU4NTk0NTI2NzgxNzIzMzgzIiwiZXhwIjoxNjUzNDI2ODQwLCJpYXQiOjE2NTM0MjMyNDAsImlzcyI6Imh0dHBzOi8vYWNjb3VudHMuZ29vZ2xlLmNvbSIsInN1YiI6IjEwNTM1ODU5NDUyNjc4MTcyMzM4MyJ9.c-zxdjjUPT7B7g9BlHFjYj2bVnCksr0RNuGtF2I-ln3dcAzgu1pd_E-zoWR-KwJDZOuSMPDcjUea75DUt5ps4TwbHFyZ1x5GD3BRArl1Ts0p_QAtND-elV2c_ZDk-txpGCkI2ESGKszjv5_UF_aiIeO5l344ECB_zERD5LA3BeXoVDix-v5uw0KLFjZM03OBcNbItdy1B7dNIGUqOZNpRp2PWXxY5ppf33BXXY3U_JepzK0qynZCvlPAeSJKqIc5LKpPBauzUYOYq0VH1xkL_SdfDgvoSCi69Eqgu9i3qNSaV8B7mdYO5mrfxsaE9SroKR2P0PdyEt-n2HkrqQAZ7w
[2022-05-24 20:14:00.828][629][debug][jwt] [source/extensions/filters/http/jwt_authn/authenticator.cc:167] google-jwt: Verifying JWT token of issuer https://accounts.google.com
============================== Get and Cache JWK
[2022-05-24 20:14:00.828][629][trace][filter] [source/extensions/filters/http/common/jwks_fetcher.cc:27] JwksFetcherImpl
[2022-05-24 20:14:00.828][629][trace][filter] [source/extensions/filters/http/common/jwks_fetcher.cc:41] fetch
[2022-05-24 20:14:00.828][629][debug][filter] [source/extensions/filters/http/common/jwks_fetcher.cc:60] fetch pubkey from [uri = https://www.googleapis.com/oauth2/v3/certs]: start
[2022-05-24 20:14:00.828][629][debug][router] [source/common/router/router.cc:467] [C0][S15262186142634120070] cluster 'jwt.www.googleapis.com|443' match for URL '/oauth2/v3/certs'
[2022-05-24 20:14:00.828][629][debug][router] [source/common/router/router.cc:670] [C0][S15262186142634120070] router decoding headers:
':path', '/oauth2/v3/certs'
':authority', 'www.googleapis.com'
':method', 'GET'
':scheme', 'http'
'x-envoy-internal', 'true'
'x-forwarded-for', '10.128.0.2'
'x-envoy-expected-rq-timeout-ms', '5000'
[2022-05-24 20:14:00.835][629][trace][http] [source/common/http/http1/codec_impl.cc:1353] [C1] status_code 200
[2022-05-24 20:14:00.835][629][trace][http] [source/common/http/http1/codec_impl.cc:1363] [C1] Client: onHeadersComplete size=12
[2022-05-24 20:14:00.835][629][debug][router] [source/common/router/router.cc:1351] [C0][S15262186142634120070] upstream headers complete: end_stream=false
[2022-05-24 20:14:00.835][629][debug][http] [source/common/http/async_client_impl.cc:101] async http request response headers (end_stream=false):
':status', '200'
'vary', 'X-Origin,Referer,Origin,Accept-Encoding'
'server', 'scaffolding on HTTPServer2'
'x-xss-protection', '0'
'x-frame-options', 'SAMEORIGIN'
'x-content-type-options', 'nosniff'
'date', 'Tue, 24 May 2022 20:13:47 GMT'
'expires', 'Wed, 25 May 2022 01:46:27 GMT'
'cache-control', 'public, max-age=19960, must-revalidate, no-transform'
'content-type', 'application/json; charset=UTF-8'
'age', '13'
'accept-ranges', 'none'
'transfer-encoding', 'chunked'
'x-envoy-upstream-service-time', '6'
============================== Verify JWK
[2022-05-24 20:14:00.836][629][debug][filter] [source/extensions/filters/http/common/jwks_fetcher.cc:85] onSuccess: fetch pubkey [uri = https://www.googleapis.com/oauth2/v3/certs]: success
[2022-05-24 20:14:00.836][629][debug][filter] [source/extensions/filters/http/common/jwks_fetcher.cc:91] onSuccess: fetch pubkey [uri = https://www.googleapis.com/oauth2/v3/certs]: succeeded
[2022-05-24 20:14:00.837][629][debug][jwt] [source/extensions/filters/http/jwt_authn/authenticator.cc:313] google-jwt: JWT token verification completed with: OK
[2022-05-24 20:14:00.837][629][debug][jwt] [source/extensions/filters/http/jwt_authn/filter.cc:110] Jwt authentication completed with: OK
[2022-05-24 20:14:00.837][629][trace][http] [source/common/http/filter_manager.cc:70] [C0][S2732626836338267029] continuing filter chain: filter=0x46903f9407e0
============================== Send Client Response
[2022-05-24 20:14:00.837][629][debug][http] [source/common/http/filter_manager.cc:952] [C0][S2732626836338267029] Sending local reply with details direct_response
[2022-05-24 20:14:00.837][629][trace][misc] [source/common/event/scaled_range_timer_manager_impl.cc:60] enableTimer called on 0x46903f4ac180 for 300000ms, min is 300000ms
[2022-05-24 20:14:00.837][629][debug][http] [source/common/http/conn_manager_impl.cc:1516] [C0][S2732626836338267029] encoding headers via codec (end_stream=false):
':status', '200'
'content-length', '2'
'content-type', 'text/plain'
'date', 'Tue, 24 May 2022 20:14:00 GMT'
'server', 'envoy'
[2022-05-24 20:14:00.837][629][debug][pool] [source/common/http/http1/conn_pool.cc:53] [C1] response complete
References
This site supports webmentions. Send me a mention via this form.