Exempting Application Default Credentials for Google MFA Reauth
2022-04-20Monday, September 16, 2019
Back in 2019, Google announced a way to force users to get periodically get prompted to reauthenticate (preferably multi-factor). For details, see Control session length for Google Cloud Console and gcloud CLI
Thats a really great…it helps with security, it helps prevent phishing it helps protect very secure apps..
For example, your domain administrator could say “make sure users who access the Cloud COnsole need to reauthenticate every day by touching the Titan Key”… or “make sure users accessing gcloud cli touch the MFA key every hour”.
However, note that this only applies to users and not service accounts (MFA doens’t mean anything for 2LO Service Account flows.). That is, this only applies to users who used Oauth2 3LO and really for browsers and first party applications google Cloud provides By first party application, i mean gcloud, gsutil, bq. In those systems, your users will see a direct reauth prompt like this
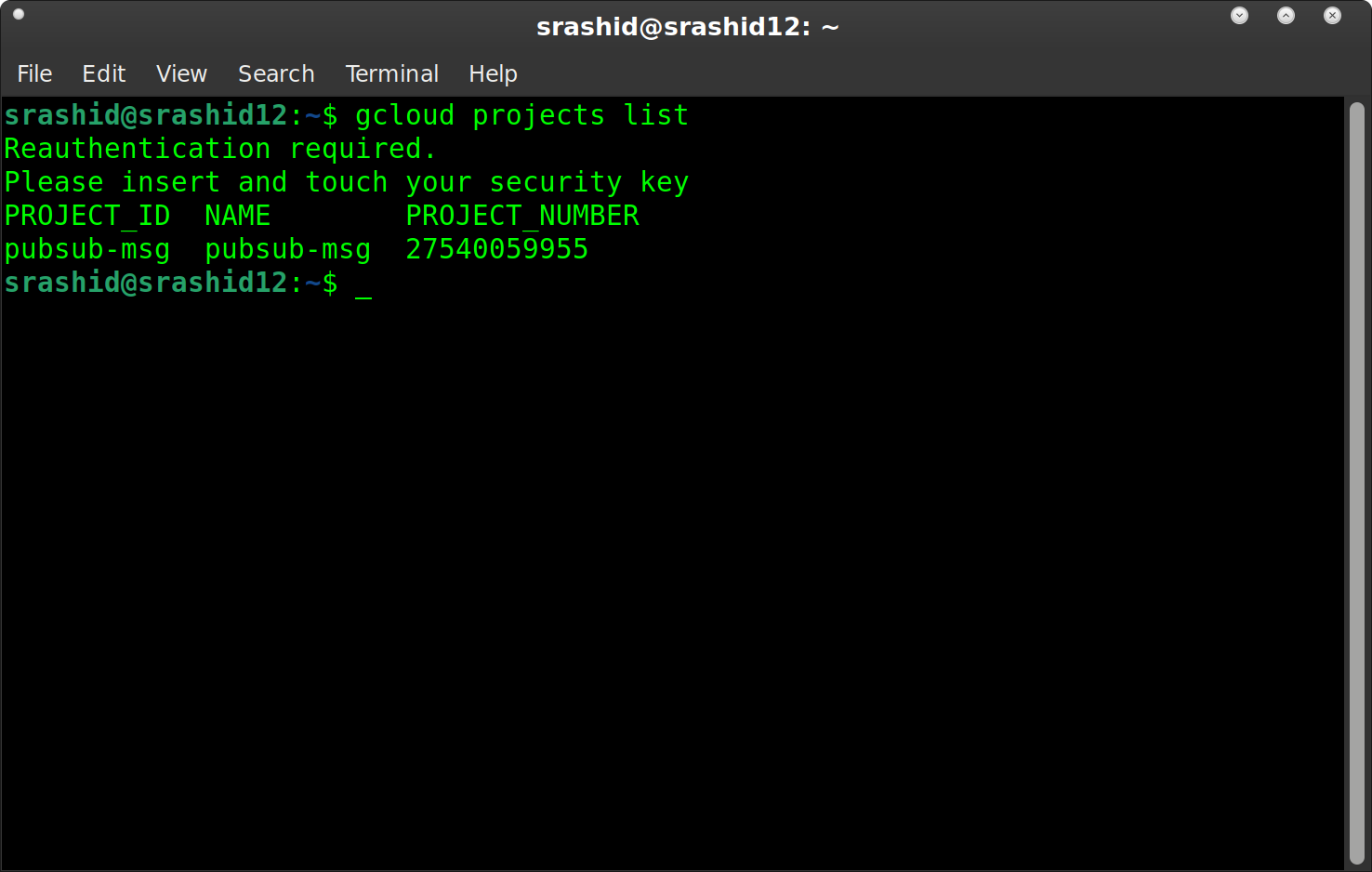
reauth prompt
But…what happens if you are using application default credentials and a google cloud client library?
How does a client library that google provides prompt a user for reauth?
The short answer is…it doesn’t..the user is left with this gem of an error to work with:
{
"error": "invalid_grant",
"error_description": "reauth related error (invalid_rapt)",
"error_subtype": "invalid_rapt"
}
jpassing explained the general issue with 3rd party apps and reauth here:
What this article is about how to place exemptions for 3LO reauth for “trusted applications” as vaguely hinted at here
Note, you’re basically bypassing the reauth security policies by doing this..its not a good idea to permanently allow this exemption and look at using embedded service accounts. …or, you know simply run gcloud auth application-default login again when you see that error.
Anyway, when you login as a user to ADC (gcloud auth application-default login), your oauth2 flow is associated with a specific oauth2 client_id:
764086051850-6qr4p6gpi6hn506pt8ejuq83di341hur.apps.googleusercontent.com
Yes, that specific client_id is used everytime you’re using ADC as a user.
So..we need to somehow place an exemption for the client_id in the workspace config.
To do that, first check the Exempt Trusted Apps in workspace
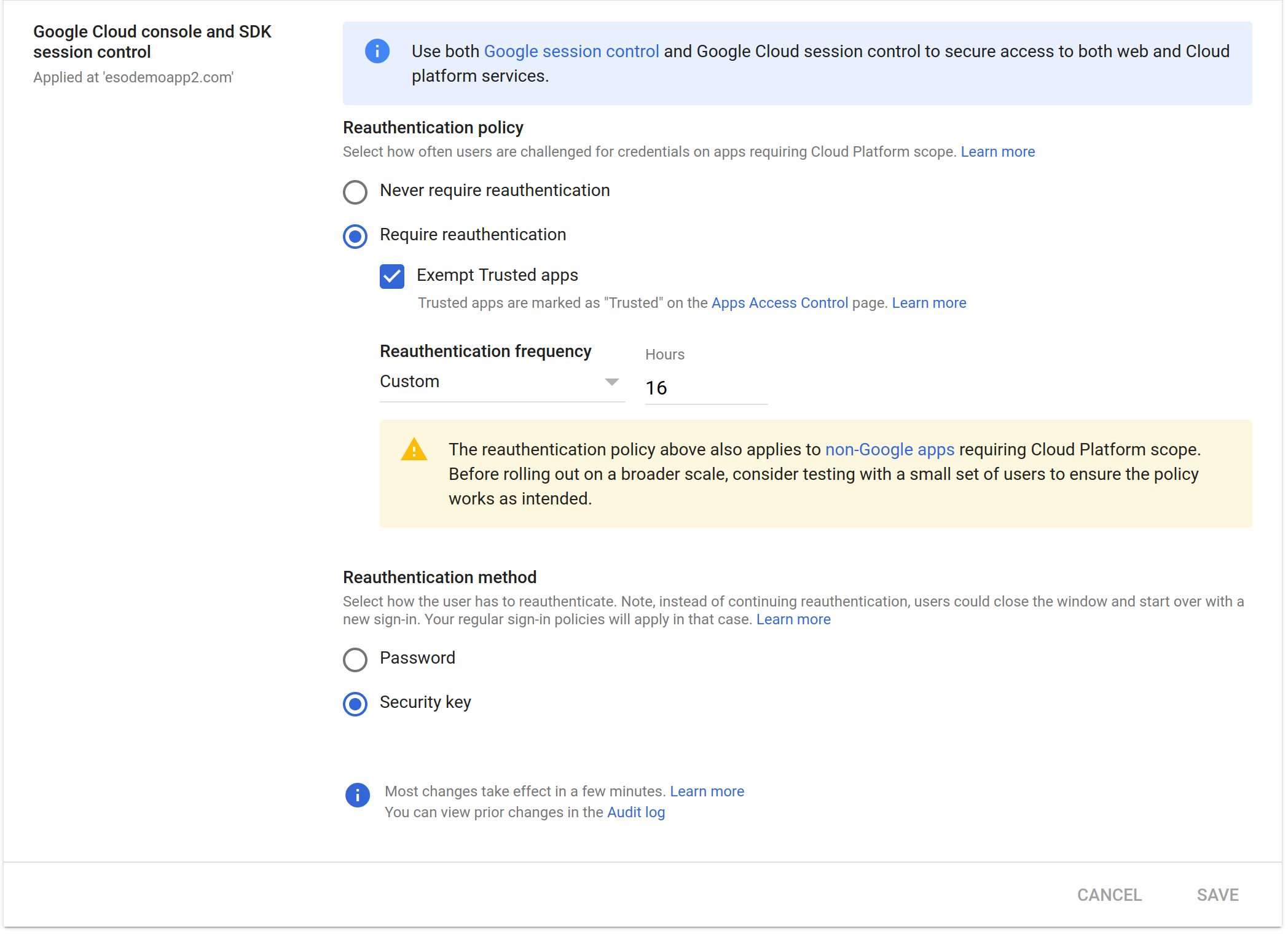
reauth bypass
And then place that client_id as a trusted app
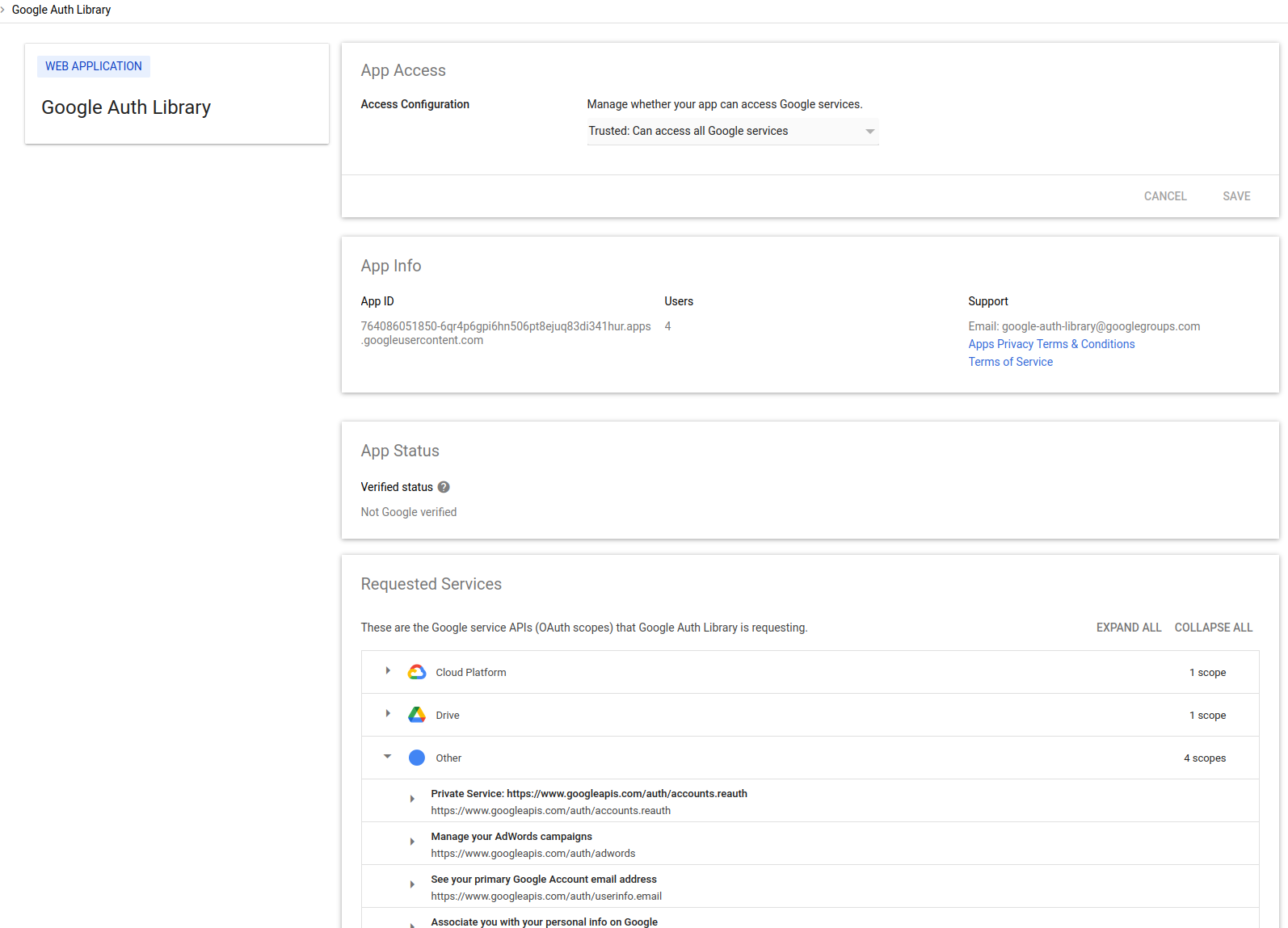
exempt trusted client_id
From then on, if you use any Cloud SDK Library which inturn uses your user credentials, you will not see a prompt for that.
Now..is it a good idea to do this?
Not really, you’re bypassing the security controls in place for just such a thing (eg, make sure a user who authenticates has MFA).
The easiest workaround is to NOT enable this bypass and just run gcloud auth application-default login to renew your credentials and refresh_token ADC uses. I realize its a bit awkward its worth not doing this exemption.
Other References
- Set session length for Google Cloud services
- Set session length for Google services
- Simple webauthn demo app on Cloud RUn
You can also access GCP services using a service account that is embedded into hardware:
This site supports webmentions. Send me a mention via this form.